728x90
Amazon S3로 Terraform 백엔드 구성하기
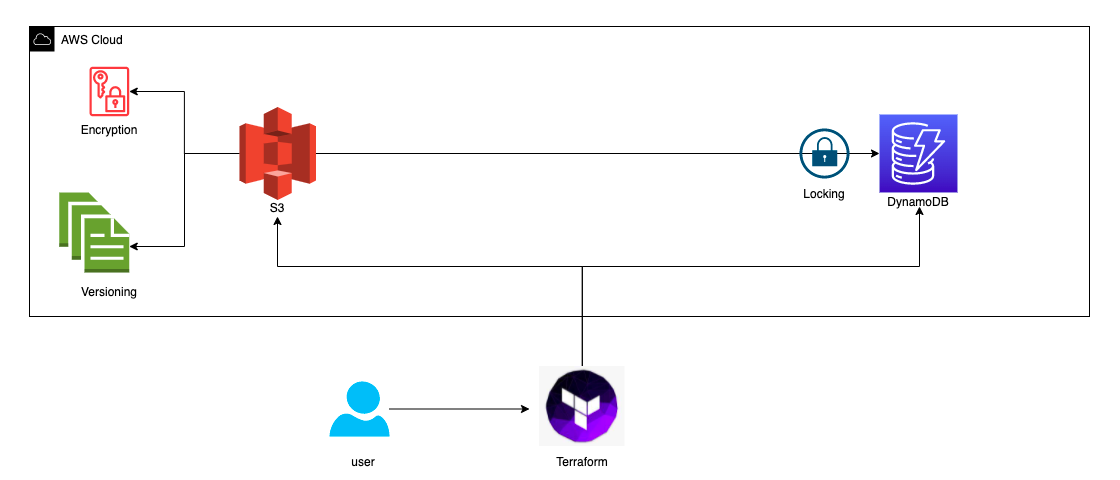
전체 조건(pre requisites)
- terraform
- aws 계정
- awscli
- s3
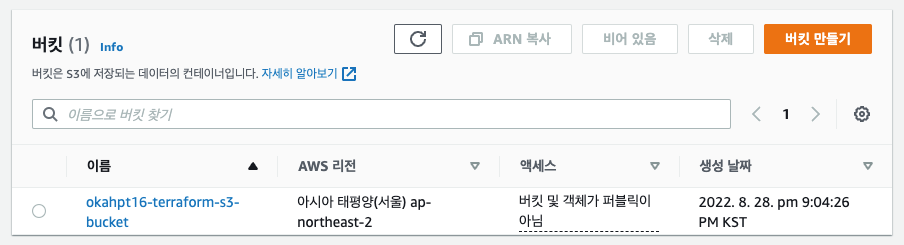
s3 버킷 생성
버킷 이름 : okahpt16-terraform-s3-bucket
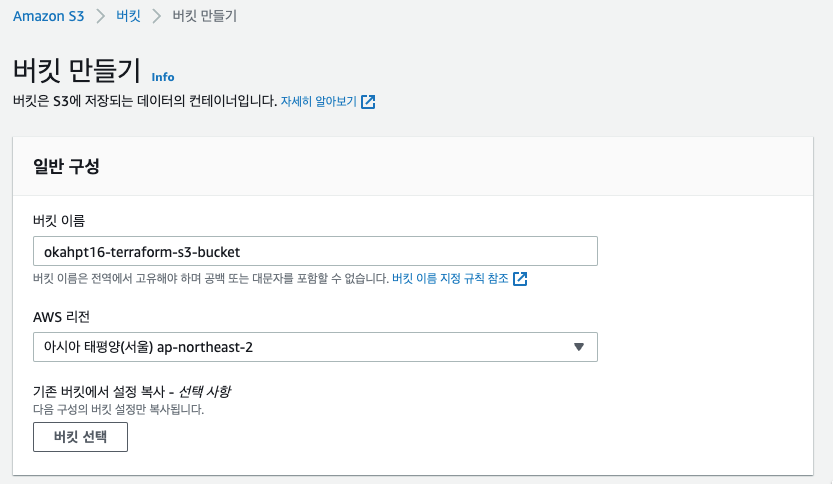
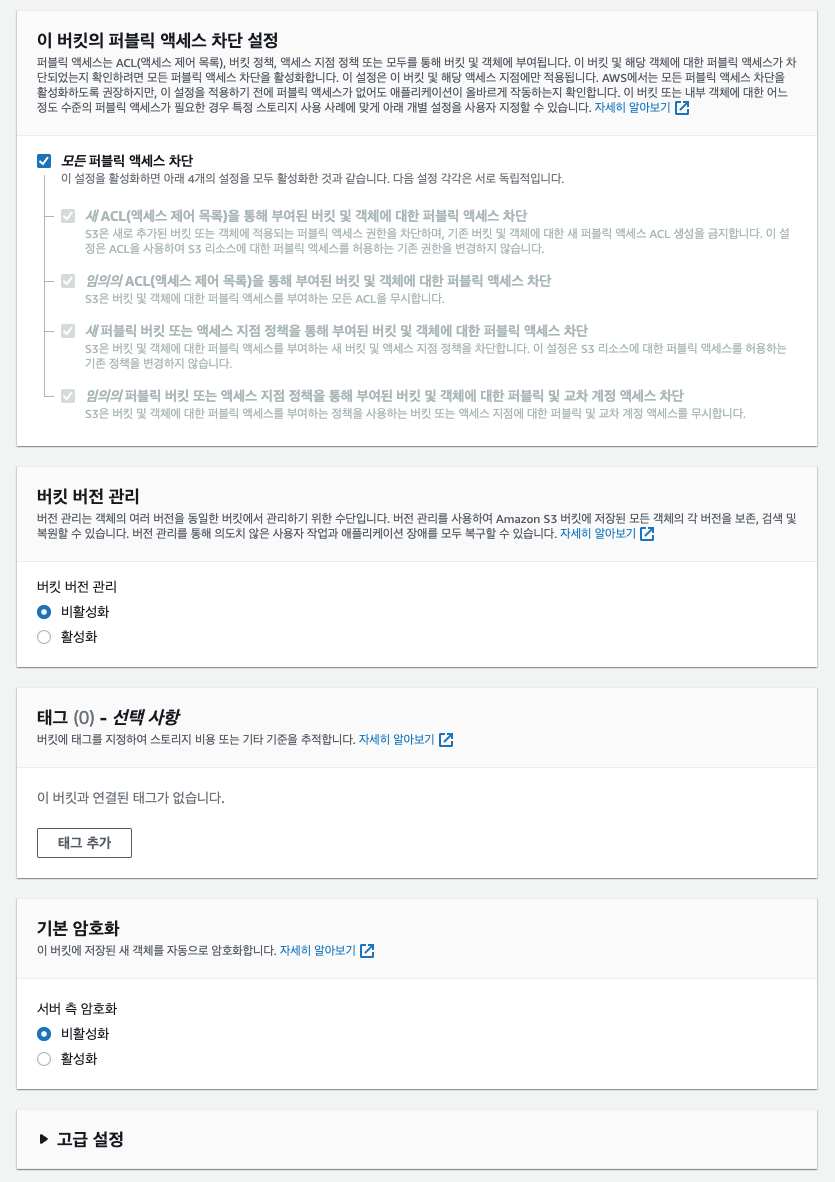
s3 버킷
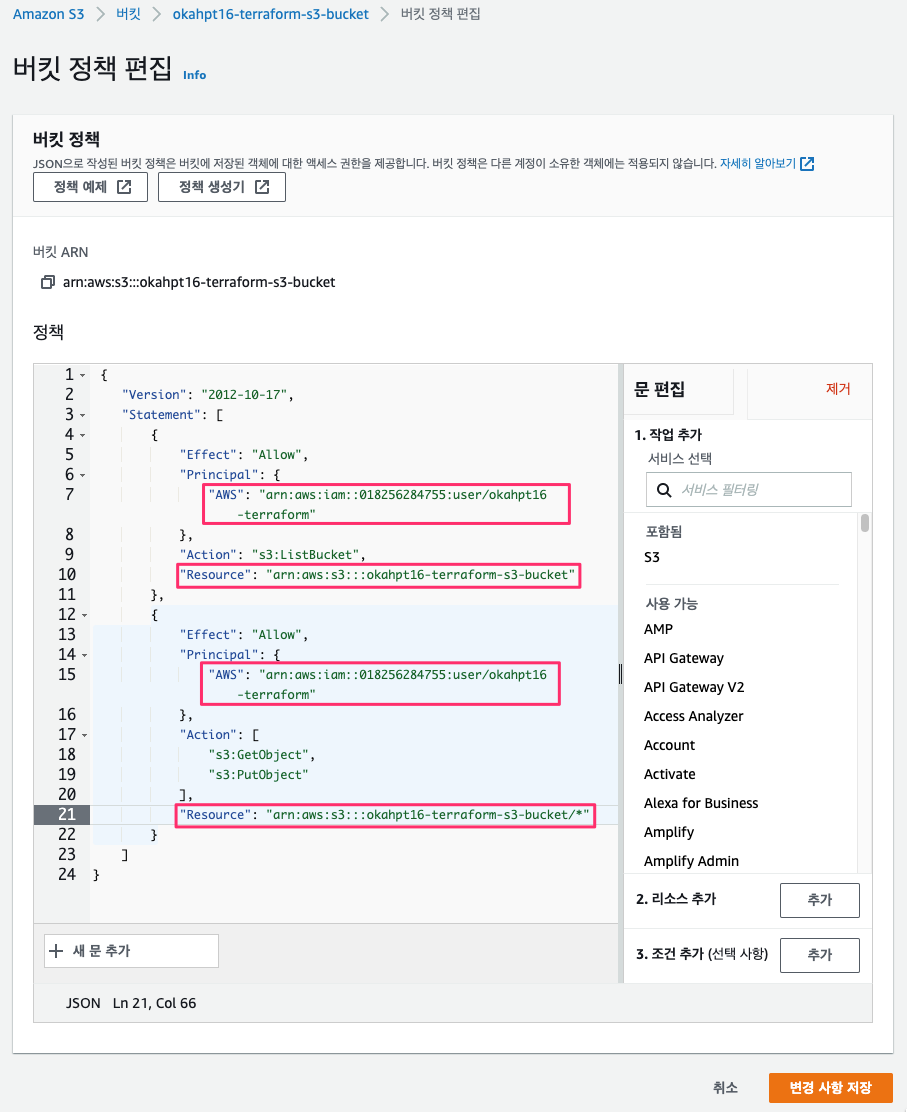
s3 버킷 정책 수정
aws --profile terraform sts get-caller-identity$ aws --profile terraform sts get-caller-identity
{
"UserId": "ZIDAQHSHTHBEMHSPLP23T",
"Account": "018256284755",
"Arn": "arn:aws:iam::018256284755:user/okahpt16-terraform"
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::018256284755:user/okahpt16-terraform"
},
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::okahpt16-terraform-s3-bucket"
},
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::018256284755:user/okahpt16-terraform"
},
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": "arn:aws:s3:::okahpt16-terraform-s3-bucket/*"
}
]
}
dynamoDB 테이블 생성
테이블 이름 : okahpt16_terraform_lock
파티션 키 : LockID
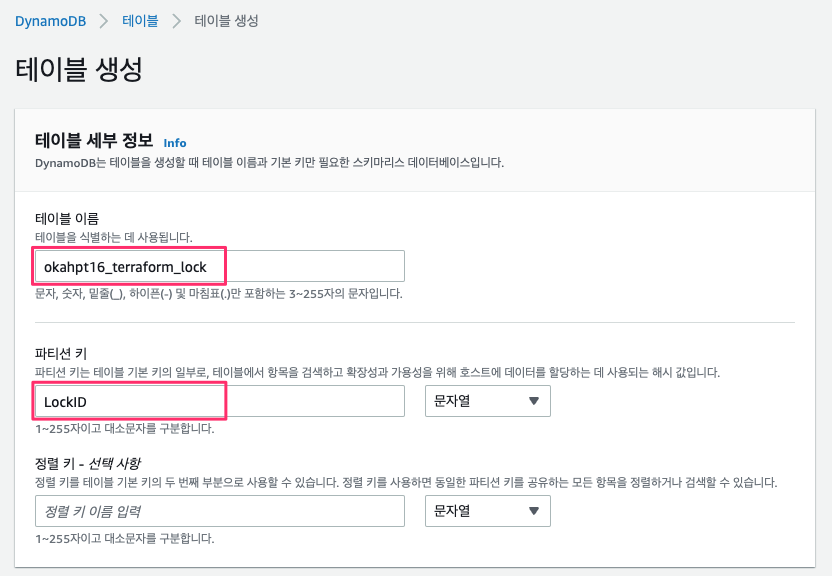
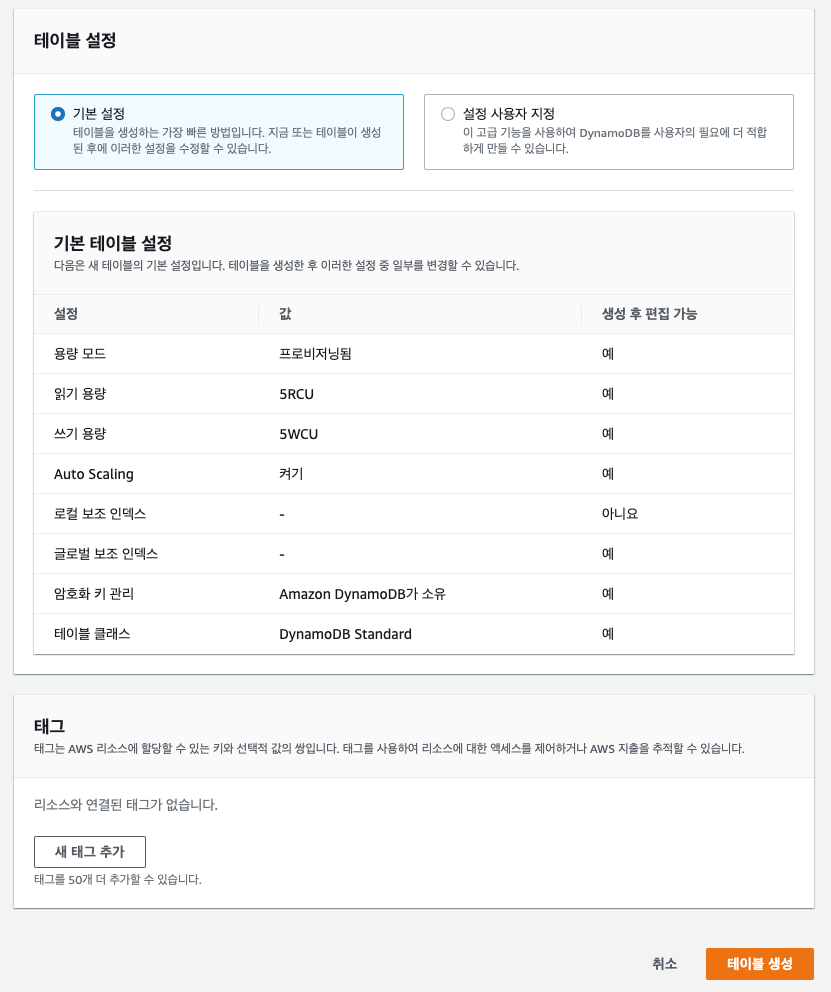
dynamodb 테이블
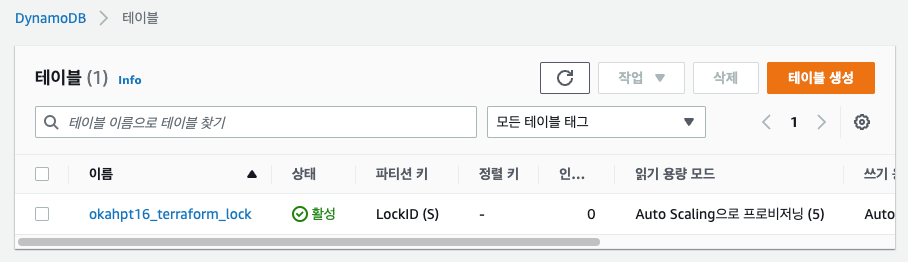
terraform backend 구성
provider.tf 파일 생성
touch provider.tfprovider.tf 파일 편집
vim provider.tfterraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.27.0"
}
}
backend "s3" {
bucket = "okahpt16-terraform-s3-bucket"
key = "terraform/kr/terraform.tfstate"
region = "ap-northeast-2"
encrypt = true
dynamodb_table = "okahpt16_terraform_lock"
profile = "terraform"
}
}
provider "aws" {
# Configuration options
profile = "terraform"
region = "ap-northeast-2"
/* shared_credentials_file = "~/.aws/credentials" */
}terraform init$ terraform init
Initializing the backend...
Successfully configured the backend "s3"! Terraform will automatically
use this backend unless the backend configuration changes.
Initializing provider plugins...
- Finding hashicorp/aws versions matching "~> 4.27.0"...
- Installing hashicorp/aws v4.27.0...
- Installed hashicorp/aws v4.27.0 (signed by HashiCorp)
Terraform has created a lock file .terraform.lock.hcl to record the provider
selections it made above. Include this file in your version control repository
so that Terraform can guarantee to make the same selections by default when
you run "terraform init" in the future.
Terraform has been successfully initialized!
You may now begin working with Terraform. Try running "terraform plan" to see
any changes that are required for your infrastructure. All Terraform commands
should now work.
If you ever set or change modules or backend configuration for Terraform,
rerun this command to reinitialize your working directory. If you forget, other
commands will detect it and remind you to do so if necessary.terraform fmtterraform planterraform apply -auto-approve$ ls -al
drwxr-xr-x 6 staff staff 192 8 28 22:01 .
drwxr-xr-x 5 staff staff 160 8 28 21:34 ..
drwxr-xr-x 4 staff staff 128 8 28 21:55 .terraform
-rw-r--r-- 1 staff staff 1184 8 28 21:55 .terraform.lock.hcl
-rw-r--r-- 1 staff staff 658 8 28 21:57 main.tf
-rw-r--r-- 1 staff staff 549 8 28 21:55 provider.tf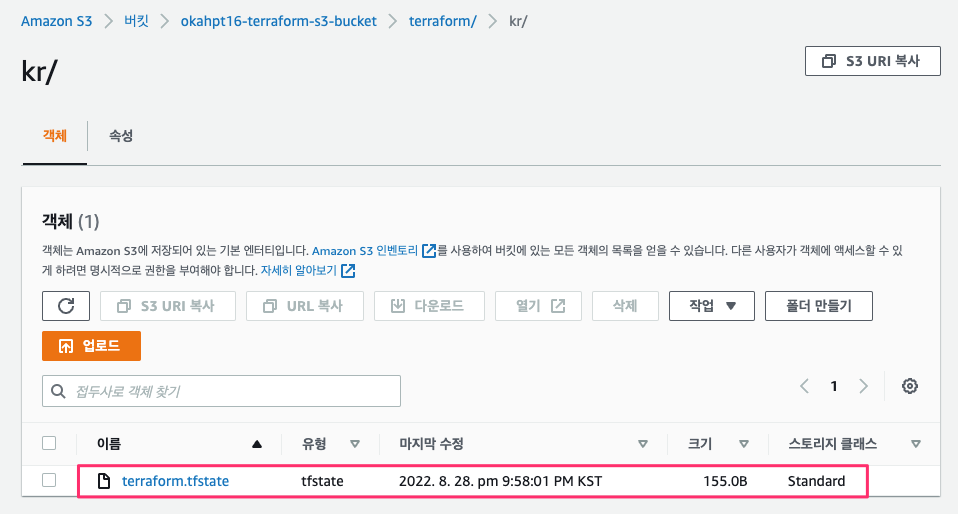
참고URL
- https://www.terraform.io/language/settings/backends/s3
728x90
'퍼블릭 클라우드' 카테고리의 다른 글
| AWS Billing(Budgets) 알람을 설정하는 방법 (0) | 2022.08.29 |
|---|---|
| [iac] Amazon S3로 Terraform 백엔드 구성하기 - terraform code (0) | 2022.08.28 |
| [iac][terraform] aws provider 생성 (0) | 2022.08.26 |
| Amazon Route 53 Invalid Change Batch 오류(InvalidChangeBatch 400) (0) | 2022.08.19 |
| [aws] AWS CodeDeploy 사용법 (0) | 2022.08.19 |



